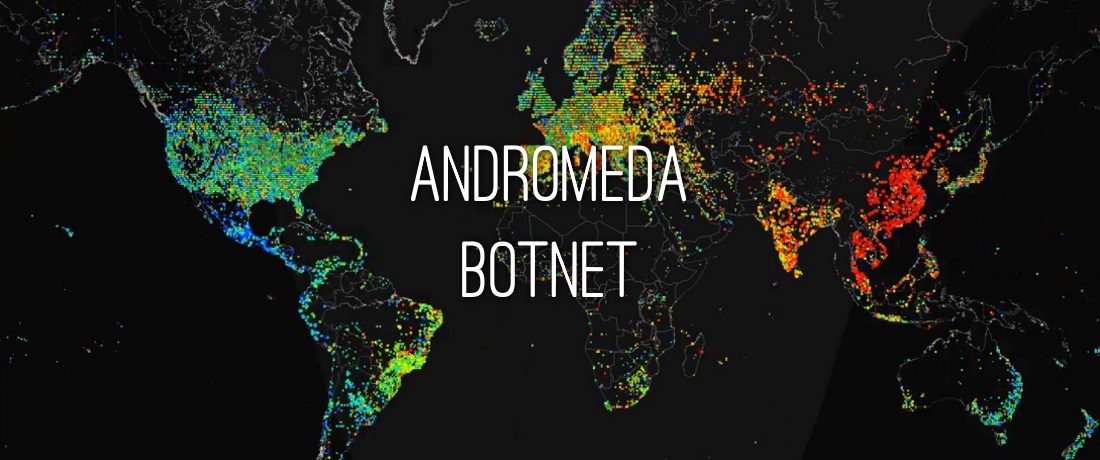
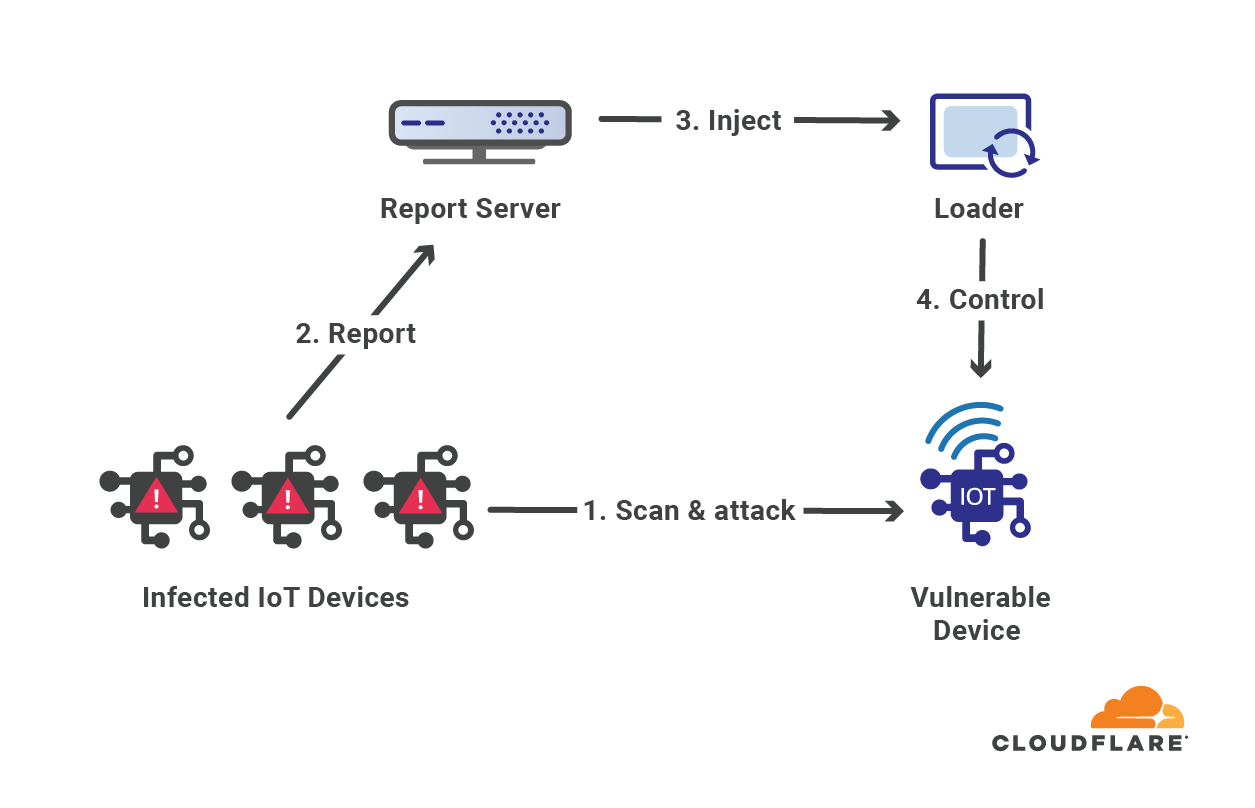
A survey of IT early warning systems: architectures, challenges, and solutions - Ramaki - 2016 - Security and Communication Networks - Wiley Online Library

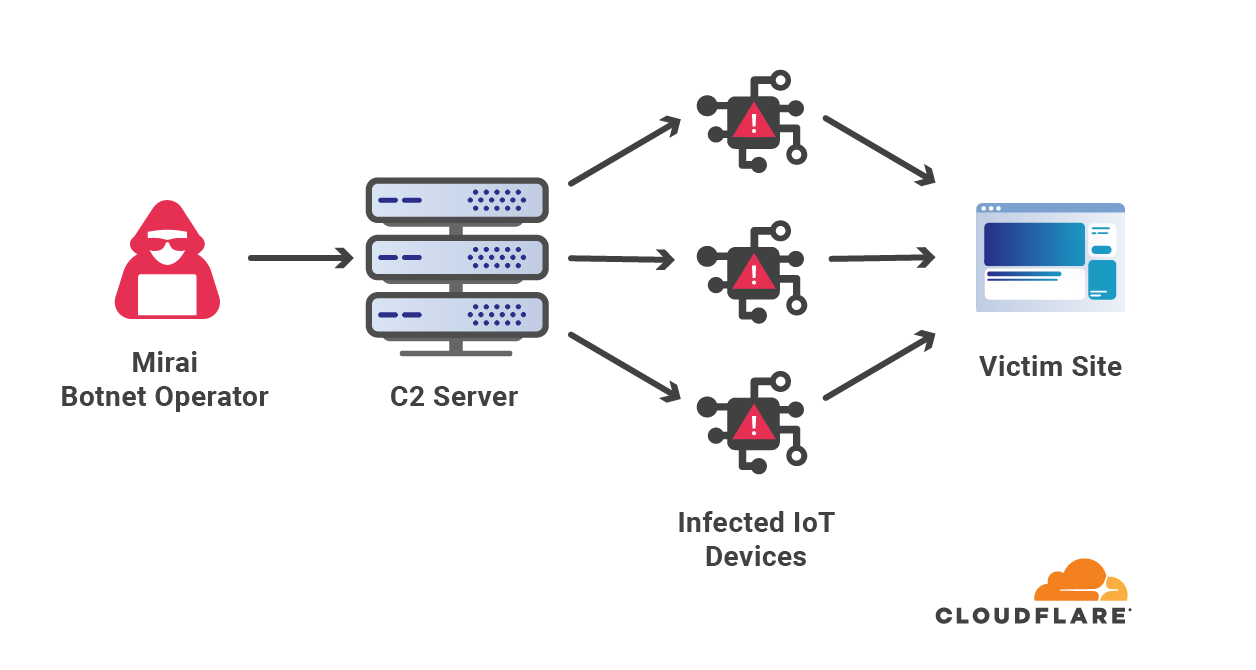
The Mirai Botnet Malware DDoS workflow, adapted from Level 3 Threat... | Download Scientific Diagram

A simplified model of a botnet conducting a DDoS attack. Once an army... | Download Scientific Diagram
![PDF] Enhanced PeerHunter: Detecting Peer-to-Peer Botnets Through Network-Flow Level Community Behavior Analysis | Semantic Scholar PDF] Enhanced PeerHunter: Detecting Peer-to-Peer Botnets Through Network-Flow Level Community Behavior Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cbae472c33300d5d6670eb14ee8397dba24cd3d5/13-TableXIV-1.png)